Hacks within the cryptocurrency domain are very frequent. Recently, a decentralized music platform Auduis suffered as it lost 18.5 million AUDIO tokens ($6m) following a malicious attack.
Broken strings
On 24 July, the Audius community treasury lost a significant amount due to an exploit in the contract initialization code that allowed repeated invocations of the “initialize” function. The respective team shared this development on the social media platform.
Hello everyone – our team is aware of reports of an unauthorized transfer of AUDIO tokens from the community treasury. We are actively investigating and will report back as soon as we know more.
If you’d like to help our response team, please reach out.
— Audius 🎧 (@AudiusProject) July 24, 2022
Different agencies/firms took efforts to release their post-mortem report for a deep analysis behind the said attack.
A crypto and blockchain security analytic platform named Certik released a simple overview to highlight the same.
The @AudiusProject has been exploited for a total of ~$6M worth of AUDIO tokens, the tokens were sold for 705 ETH.
The attacker modified the Audius governance contract’s configurations, then proposed and executed a malicious proposal draining 18.5M AUDIO. pic.twitter.com/djuAO1Jarv
— CertiK Alert (@CertiKAlert) July 24, 2022
Here, the attacker modified the Audius governance contract’s configurations, then proposed and executed a malicious proposal draining 18.5m AUDIO.
This allowed an attacker to modify the voting system and set erroneous stake values in the network.
Ergo, leading to a malicious transfer of 18m AUDIO tokens held by the Audius governance contract (referred to as the “community treasury”) in their wallet.
Later, the attackers were able to do a proposal, pass it, send themselves all the treasury tokens, then dump it on Uniswap in one transaction. Notably, the attacker sold 18m AUDIO tokens for 705 ETH ($1.1m).
It seems like $6M in $Audio were only traded for just a little over $1M in ETH. https://t.co/eAQDvBoTJ6 pic.twitter.com/gRf4yw3Qdv
— MistTrack🕵️ (@MistTrack_io) July 24, 2022
In addition, another firm, Go+ Security too shared a brief analysis on 24 July to highlight the said attack. In a blog, the firm added a small flowchart asserting the full attack vector.
Tamper with vote parameters -> submit malicious proposal -> Tamper with vote weight -> Vote -> Execute proposal
The firm further added an in-depth analysis including screenshots of the aforementioned timing of the unfortunate event. Another blockchain investigator Peckshield narrowed down the fault to Audius’ storage layout inconsistencies.
The issue of @AudiusProject lies in inconsistent storage layout between its proxy and impl. In particular, the collision of Audius Community Treasury contract results in an equivalence of disabling the initializer modifier. The proxyAdmin addr (0x..abac) plays a role here. pic.twitter.com/x4CqRncahp
— PeckShield Inc. (@peckshield) July 24, 2022
Damage control?
The Audius team updated that the vulnerabilities were patched, but many features such as token transfer and balance display have not been activated because of concerns about risks.
“This was achieved by “proxy-upgrading each contract to a minimal BlockingContract that did not contain the same bug. This prevented further repeated invocations after relegating proxyAdmin control to a predefined address owned by the team.”
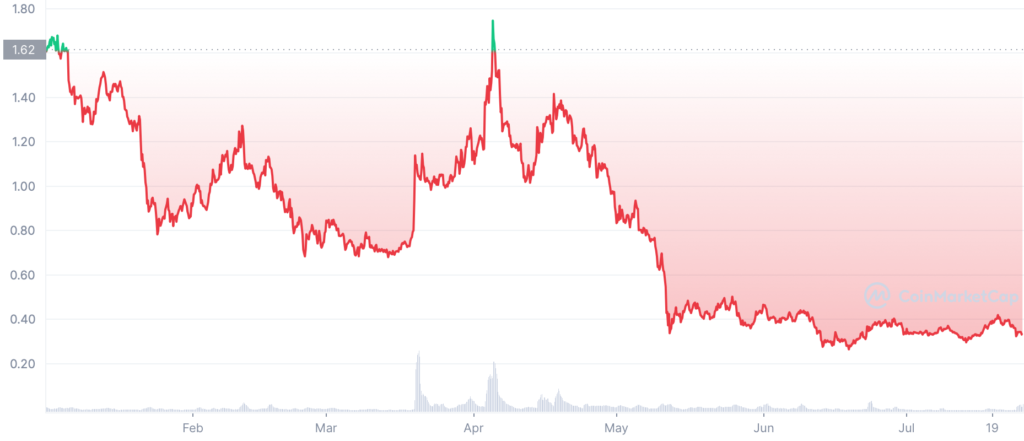
But did it help the affected token? Well not really. The token witnessed a massive fall on CoinMarketCap as evident in the graph below.
At the time of writing, the token (AUDIO) suffered a fresh 2% correction as it slid past the $0.33 mark.