It’s been a while since the crypto community witnessed the unfortunate Ronin Network hack on 29 March. The blockchain underlying the popular crypto game Axie Infinity lost 173,600 Ethereum (ETH) and 25.5 million USDC. Ergo, crossing the exploit sum to more than $600 million.
On 14 April, the U.S. Department of Treasury’s Office tied the North Korea-based hacking group, Lazarus, to the Ronin Network exploit. The Office of Foreign Assets Control (OFAC) added an Ethereum wallet address (0x098B716B8Aaf21512996dC57EB0615e2383E2f96) associated with Lazarus to its sanctions list.
And then what?
…here’s the sad part, despite this lockdown, the attacker(s) behind the crypto industry’s largest exploit moved the stolen loot through anonymizing services. Although, following a redundant pattern: From a sanctioned address to an intermediate address and then sending the funds to Tornado Cash.
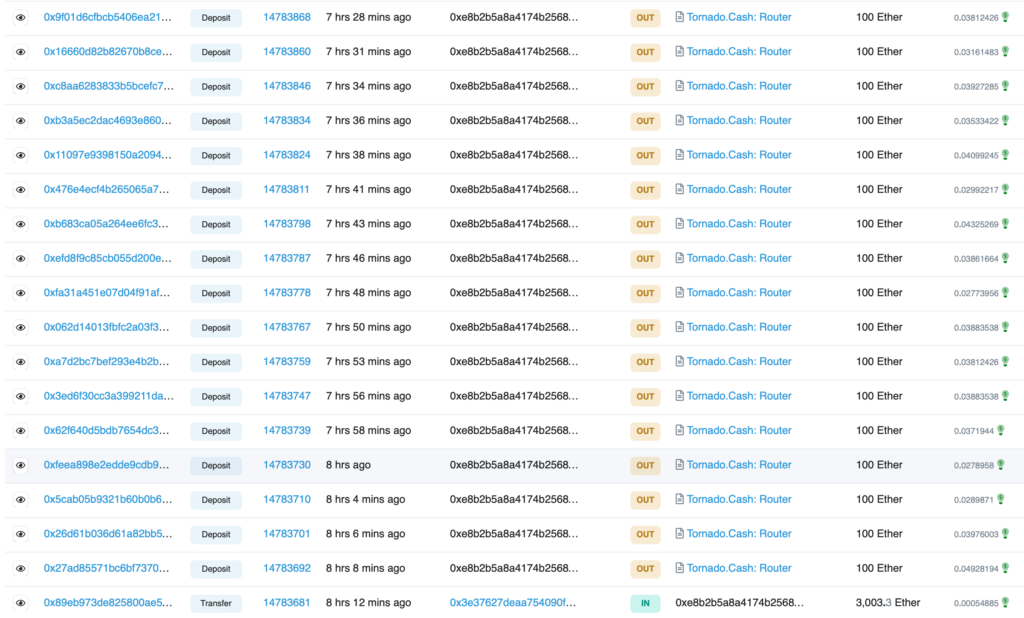
Wu Blockchain, a famed news agency, on 16 May highlighted yet another transfer concerning the “same” address. The Ronin attacker transferred 3,003 ETHs to the new address 0xE8B2B5A8a4174b256828Fca0F40a8831521160e5. Later, transferred 100 ETHs to Tornado Cash as showcased here:
Source: Etherscan
Most hackers use the Tornado Cash privacy tool to wash illicit crypto funds from the hacking. The tool divides the on-chain link between a source and destination address. This allows hackers to camouflage their addresses while converting illicit crypto funds into fiat.
Just three weeks ago, the alleged hacker transferred 33,568 ETH to a new address as per Etherscan. Prior to that, the hacker cashed in 28,164 ETH and 2000 ETH over different intervals. At present, only 2.2 ETHs are left in the current address.
Ignoring the lockdown?
Well, that’s exactly what’s happening. The U.S Treasury Department’s Office of Foreign Asset Control (OFAC) had added the solitary Ethereum address to its ‘Specially Designated Nationals’ list. But, looks like, the hacker/hackers have continued to ignore such warnings.
What’s next?