Crypto custody is now a big deal. There are huge changes happening as to how we store wealth, says Adrian Pollard, the co-founder of HollaEx.
Long ago people liked to store their wealth in the heaviest and hardest of elements – diamonds, silver and gold – and lock them away in a secluded vault. The heavier the better. Heavy is reliable, it feels safe, heavy is fit for generational wealth and this was true for centuries, that was until magical internet money came along…
Mere Numbers on a Screen
It is safe to say that our love affair for heavy metals began to wane as soon as paper money came into play. Not long after that, our trust extended beyond printed numbers on paper to trusting digits on an ATM screen. Before we even knew it we were all trusting what is displayed on our phone’s banking apps.
This shift from the heavy physical stuff, to the feather-light paper bank note, to numbers on a screen was a great leap of faith. It was strengthened by the convenience and speed that the digital medium grants. Who wants to carry heavy gold bars around, or even a pocket full of teeny-tiny metal coins?
Now that we are down to trusting digits, what’s next? Some would say blockchain-based assets like Bitcoin are the next means of storing wealth. A digital gold if you will. But the issue with securing this digital gold is that it requires tricky and unintuitive storage practices.
Ironically, despite Bitcoin being digital, it seems these days to often take a more physical form. Why? Because physicality leads to intuitive solutions.
Here are some of the smart and unusual hybrid digital and physical money storage methods practiced in the wild by individuals and big businesses.
Crypto custody: Open Sesame
The truth is securing crypto isn’t that dissimilar to securing gold in a vault. Instead of metal keys to a vault, there are instead digital keys. These keys can take many forms, like a QR code or simply a few random English words akin to a very long password.
Input the correct secret words within any crypto wallet and like magic, you’ll be granted access to the treasures inside. These secret words are like the famous phrase ‘Open Sesame’, giving entry to locked-away treasures.

These 12 words (the ‘secret key’) are often stored on USB-like devices, written on loose pieces of paper, or engraved on sheets of metal and hidden away in a location only known by the coin owner. But just like in the Arabian Nights tale Ali Baba, thieves can very easily eavesdrop and learn about other people’s secret words and gain access to other people’s treasure. This eavesdropping is the origin of many of the crypto hack stories seen in the media and emphasizes the importance of keeping malicious parties in the dark.
The truth is many crypto storage solutions are very low-tech, and this article plans to uncover a few of the unexpected trade secrets of the crypto custody businesses.
Before we uncover any secrets, a review of crypto storage basics is long overdue. There is no better place to start than with the terms custodian, non-custodian, single, and multi-sig.
Multi-Signature – Non-Custodial
First, non-custodial or ‘self-custody’ is the act of securing (holding) your own keys and coins. It means you or a trusted team of people are securing the private key or keys that can take the form of 12 to 24 words mentioned previously in this article.
Self-custody means just that, you are not using a service provider like an exchange or bank, and instead are fully responsible for the storage and security of your assets.
There are many ways to achieve self-custody for your crypto assets, but one of the most talked about methods is the ‘multi-sig’or ‘Multi Signature’ walletmethod. This method is a favorite amongst businesses, startups, and even enterprises.
Coins on a multi-sig wallet are accessed with multiple keys. Generally, to move funds in and out of a wallet, 2 keys are required out of a total of 3 keys. These keys are typically handled within your wallet software automatically but can be extracted and put into a physical format like paper. When putting your keys onto physical media, remember to keep it as secure as you would the keys to your own bank vault. Just as with a vault, having access to the keys means having full access to the assets they are supposed to keep safe.
Crypto Custody: It Takes Two to Tango
So how does multi-sig work when you want to move the coins? One way to think of the multi-sig process is to think of it as a missile launch process. Obviously, a missile launch is a sensitive action that takes at least two people to confirm the launch, a two-to-tango situation if you will.
A multi-sig wallet can even have 10 people holding 10 different keys with 5 keys being the requirement to move the wallet’s coins. With 10 keys, it is easy to imagine that things can get complicated. More keys won’t necessarily equate to better safety. But it illustrates the depth of possibilities available in crypto wealth storage.
This guide by Unchained Capital tries to measure the effectiveness of key count (also known as ‘redundancy’) with the ratio of required keys (how many keys are needed simultaneously to move coins).
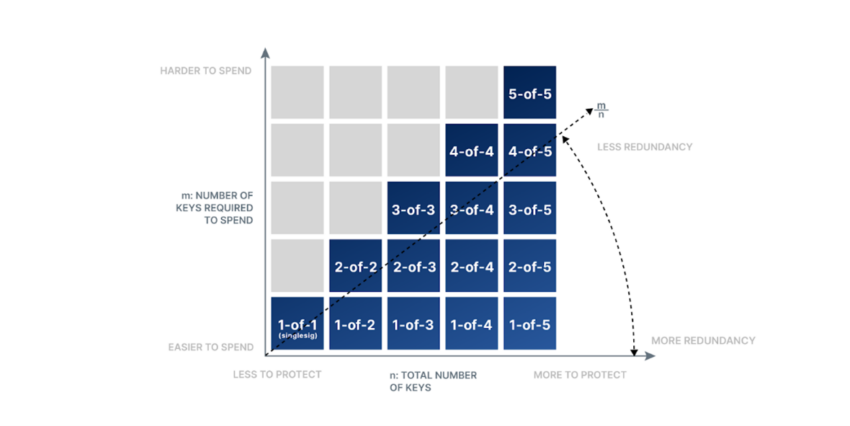
In short, the more required keys are needed, the stronger the protection but with a high trade-off cost to user-friendliness, meaning coins are going to be very hard to move.
Crypto Custody and Multi-Sig: How Practical is it?
The internet itself is secured in a kind of multi-sig where 7 people hold the keys to the foundation of the entire world wide web.
If multi-sig is good enough for the security of our internet, then it is probably good enough for the security of your coins. However, multi-sig is still a tricky method of crypto storage because it is reliant on people, and people can lose keys.
Storing keys can be so tricky, even banks that are in the business of money storage are yet to offer Bitcoin storage, save for a few outliers. This goes to show that there are obvious drawbacks with multi-sig.
Here is a summary of the pros and cons of using multi-sig storage:
Pros
- Slows processes down significantly thus reducing the chance of an individual mistake
- Distributed risk and can have potentially good fail-safe aspects
- Great for large teams, businesses, and large organizations
- Experts can build in fine-grained programmatic wallet access control policies
Cons
- Tracking all the key holders/members is difficult logistically, as well as expensive
- The more complexity added to any process, the higher the chance of accidental key loss
- Less privacy as multiple people will have to know the sensitive key information
- Slow and difficult to test on a regular basis, increasing the cost of storage
- Difficult to execute urgent transactions (in some cases this could be considered a pro).
Single Key – Non-Custodial
A single key system is perfect for individuals or small teams. It is the easiest, and most commonly used method because it is part of all wallet software by default. This single key storage method comes with zero counterparty risk, meaning other people aren’t going to be a problem. This of course means responsibility is also solely with the owner of the single key.
The keys can take the form of 12 or 24 words (the more words the more secure), these words can be memorized to form what is called a ‘brain wallet’, with the keys only known in the mind of the owner. Alternatively, many owners will keep a physical or digital copy of the key, kept securely.
Having only a single key as the only requirement for accessing the fund is by far the simplest self-custody system, however, it comes with real human issues. Unexpected death for example can literally mean that coins are taken to the grave, a unique, and unfortunate feature that other money or wealth systems don’t share.
The only solution to unexpected death is to share a kind of map to the treasure, a treasure map so to speak. Only then can coins be found and passed on to others. This ironically may mean that costly legal contracts like a will are required and may mean going back to traditional institutions and lawyers again — costly!
Below are the biggest pros and cons of a single key solution.
Pros
- Good for small fortunes
- Perfect solution for small groups or an individual
- The least complex system, especially using a 12 to 24-word mnemonic system
- Can be very private and secure
- Moving funds is simpler, faster, and easier
Cons
- Single point of failure
- In the case of an unexpected fatal accident and in the absence of clear directions to the secret key (AKA, private key) coins are rendered lost forever
- Risky for large fortunes
- As funds can be very easily and quickly moved. It may be an impractical solution for people prone to impulsivity
Suffice it to say, a single key as illustrated above for one key requirement solution (highlighted blue at the bottom of the above graph) is nice and simple. The graphic also shows us that having redundancies/backup (creating more of the same key) can reduce cases of accidental key loss.
Third-party – Custodial
What is a custodial? A custodial is where you throw all the private key mumbo jumbo mentioned above and trade it all in for the simple login user experience – a username and a password. Custodial solutions are in fact how most people today store and transact in crypto.
Think the good old bank model reincarnate, where the keys aren’t your problem and recourse may come as part of the service.
What’s the catch? One must have strong faith in the institute they grant custody to.
Custodial systems are the exact reason why Robinhood, Binance, and your bank are popular. By gathering together the aspects of crypto, such crypto exchanges double as both cryptocurrency exchanges and crypto custodians, almost like a crypto bank. They offer an experience pretty close to a traditional bank which is arguably the exact reason why 95% of people prefer interacting with crypto through these centralized exchanges (CEXs) – convenience!
Besides convenience, there are other custodian pros:
Pros
- Adds more functionality to your coins (24/7 trading, earn rewards/interest, ability to convert to fiat cash, etc)
- Reasonable solution for smaller sums of money or money that needs to be ‘put to work’
- Familiar email and login user experiences, high user-friendliness.
- Recourse, account recovery, and helpline services
- Adequate for those that are frequently paying or transacting with crypto
Cons
- Potential withdrawal delays and various hidden delays, fees, and quirks
- Potential privacy issues due to having to share personal data
- Platform failure may lead to a part or complete wipeout of all your crypto funds
- Strong faith and trust in the crypto service provider (insurance funds can only go so far)
At the end of the day, using a custodian is a multifaceted trade-off between convenience, functionality, and security. For smaller amounts and for power-users that transact frequently a custodian can bring extra added benefits.
How do Crypto Custodians Work?
Now the big question, how do custody services work? In short, it’s hard to know as custodians secure their systems through obscurity and the exact methods remain a closely guarded secret.
What is commonly known, however, is that ‘cold storage’ is commonly practiced. This just means a wallet (and its internal private key) won’t be exposed to the world wide web. A cold wallet should rarely be touched and may exclusively be used for deposits for the majority of the time.
How these cold wallets are made, managed, and accessed largely remains a mystery, as the creators try to stay ahead of malicious parties who would use the knowledge to access them.
However, from what is publicly available on the internet we can get a few clues on how a couple of the largest custodians generate keys and store their cold wallets.
For example, Xapo, an established custodian, provided inklings online that at least one of their wallets is buried deep underground in a military, nuke-resistant bunker within the Swiss Alps. Underground locations seem to be a good hiding place for private keys that many other custodians are copying, separating valuable assets completely from the outside world.
Crypto Custody: Rituals of Secrecy
On the other side of the world in the US, Coinbase, the largest crypto player has come out and shared that they use electromagnetic signal blocking tents to secure their cryptocurrency wallet generation.
Through this almost esoteric ritual, the principles of electromagnetism are taken advantage of to prevent outside snooping on the contents within these tents.
Alongside the tin foil tents, Coinbase controls the power to the key-generating devices inside the tents. These unique power supplies are designed to hide power fluctuations that could leak clues about what’s happening inside the silver tent during the crypto key generation phase. Hackers can be highly intelligent individuals and therefore require high intelligence guards against them.
This key generation ritual inside the tent is called a key ceremony and where Coinbase’s private keys are forged. The ceremony is an offline-only event and done in person with a reverent group in a soundproof location with zero phones and cameras.
This, perhaps justifiably paranoid process is designed to ensure that leaks of the secret key are, without a shadow of a doubt, impossible. When billions are on the line it is worthwhile to take every precaution possible.
Crypto Custody: Secret Keys
Despite how the key ceremonies are carried out, what all custody providers do in common is that they hold multiple copies of the secret key on a range of physical mediums such as USB sticks and hard drives, metal engraving, or good old-fashioned ink on paper. These are then spread across the globe, some ironically being stored in traditional bank safety deposit boxes, or some sent deep underground, just as was done with the gold bullion of old.
Suffice to say, for the most advanced digital money in the world, on the cutting edge of technology, it can seem like a starkly contrasting mix of archaic procedures to safely generate and store digital keys. Truth be told, crypto custody is the ancient art of good old-fashioned physical security blended with digital cryptography. Bit of old, bit of new.
Crypto Custody and Securing Your Own Coins
For those of us without access to nuclear bunkers or electromagnetic blocking tents, there still exists (slightly less expensive) methods for securing these keys. These methods do require a degree of higher personal responsibility. You may trust the blockchain but do you trust your own ability to secure coins? Have you ever held your entire life savings in your hands? Anyone that has, knows the heavy feeling of responsibility. It is uncomfortable which is why most people put their trust in banks for fiat and now their crypto exchange for digital assets.
If you are happy to shoulder this burden of responsibility, what solutions are out there to ease it? Inconspicuous and novel solutions are being invented all the time such as the ‘Bolt and Washer’ method (bolt and washer is not some techie metaphor here, it’s quite literal).
Anyone well versed in crypto culture will recognize one of these storage devices where each washer is clearly stamped with a sequential number and a unique word. The washers are then assembled and bolted together and creates a strong and long-lasting method of crypto storage solution that is very unassuming.
It can be disassembled to reveal the words which can then be inputted into any wallet software for quick fund recovery. It is one of many original DIY crypto storage solutions made every day by regular people.
Unfortunately, the washer method has made the rounds on the internet which may render it less secure now that the secret is out, however it still illustrates how anyone with a little creativity can take full custody of their own coins.
The Essence of Crypto Storage
The issue with securing digital gold is that things can easily go wrong. Services can and do fail and even your trusted computer or hardware wallet device won’t last forever.
Even paper, history’s most trusted data storage is prone to fires, floods, and accidents. Life happens.
For those gifted with the confidence to believe they can memorize a dozen secret words, they should remember that memory is infamously unreliable. Even individuals endowed with photographic memory are still running the risk of accidental memory loss due to head injury or aging which may result in coins forever lost in cyberspace.
What this means is that crypto storage isn’t a one-size fits all situation. Take stock of your own situation and make the decision that best suits who you are, and what you want to secure.
For most individuals the convenience and support offered through using a crypto custodian for at least part of your funds is probably prudent. Most of us are experienced with conventional login experiences, but perhaps not as much with the intricacies or cryptocurrency. For this reason, offloading some of the responsibility to a third party can be a sigh of relief for those wanting to get involved in the crypto space.
However, you may be running a business or maybe you are part of a team, dealing with more significant amounts. It would be wise to combine various non-custodial and custodial methods. Using crypto services or open-source white-label crypto solutions will ultimately require you to trust in the platforms, but less so if using an open-source solution that has the added benefit of a long and vetted track record.
There are even free and practical solutions out there in the DeFi form that could help with business applications of crypto and can even lead to unexpected ideas around starting your own Bitcoin business.
Not Your Keys, Not Your Coins
For brave individuals, most of the time, a single key method on a hardware wallet with a backup of a paper wallet will suffice. The higher the amount though, the more redundancies should be added. This could perhaps be as simple as separating all the different wallets onto different devices and if you have someone you can trust (really trust, remember anyone with the keys has access to the funds) then allowing them to hold one wallet can help you in avoiding a total financial lockout.
To conclude, blockchain assets have introduced a new dimension of self-sovereignty into human wealth storage practices. In essence, the crypto storage mantra ‘not your keys, not your coins’ still rings true today. No matter the final method used when storing assets, it is no doubt wise to at the very least know about, and consider other methods, and to weigh up what will work best for you to keep your digital gold, yours.
About the author

Adrian Pollard is the co-founder of HollaEx, a white label open-source crypto exchange software provider. Adrian’s history in crypto spans back as far as 2013. He has been working actively in the crypto space since. Today, he manages the product design around crypto trading and open-source products which allows individuals and businesses to create crypto projects such as coins, exchanges, wallets and other common crypto-based financial products.
Crypto custody: Got something to say about choosing crypto custody, or not choosing crypto custody! Or anything else? Write to us or join the discussion in our Telegram channel. You can also catch us on Tik Tok, Facebook, or Twitter.
Disclaimer
All the information contained on our website is published in good faith and for general information purposes only. Any action the reader takes upon the information found on our website is strictly at their own risk.