Silk Road fraudster James Zhong pleaded guilty to stealing 50,000 BTC from the Silk Road darknet marketplace in 2012.
According to the U.S. Justice Department, Zhong created 140 transactions that caused Silk Road’s withdrawal processing system to deposit 50,000 BTC into his nine accounts.
Lead up to Zhong’s plea
Zhong’s guilty plea follows a seizure of roughly 50,676 BTC ($3.3 billion) by law enforcement in Nov. 2021 from his home in Gainesville, Georgia. Zhong deposited between 200 and 2000 BTC into each of his Silk Road accounts. He then made a series of rapid withdrawals within seconds of the deposits. After that, he transferred this money out of Silk Road and consolidated the funds into two large amounts.
When the Bitcoin blockchain split to create the Bitcoin Cash hard fork in 2017, Zhong received 50,000 BCH. He converted BCH to Bitcoin using overseas exchanges. This conversion took his Bitcoin holdings to 53,500 BTC, called the “Crime Proceeds,” according to the DoJ.
When law enforcement raided Zhong’s home in 2021, they found the wallet keys for 50,591 of the 53,500 BTC in an underground safe and a computer board. Additionally, they seized over $600,000 in cash, 25 physical Bitcoin, and several precious metals. Later, Zhong voluntarily handed over about 1,004 additional Bitcoin.
Zhong could face up to 20 years in prison for his crime and will face sentencing on Feb. 22, 2023.
The curious spate of Silk Road thefts
Silk Road was an online darknet marketplace founded by convicted criminal Ross Ulbricht. It peddled illicit items for Bitcoin between 2011 and 2013. A jury unanimously convicted Ulbricht in 2015, and he was sentenced to life in prison. Since then, authorities have cracked down on at least two cases of theft from the Silk Road, of which Zhong’s is the most recent.
When authorities arrested Ulbricht in a San Francisco library, they found crypto keys for only 174,000 BTC(about $105 million) of the 614,000 BTC commissions earned during Silk Road’s two-year operation.
Crypto keys are long strings of letters and numbers that authorize users to transact on a blockchain. A crypto user uses a private key to spend crypto. They use a public key to send crypto.
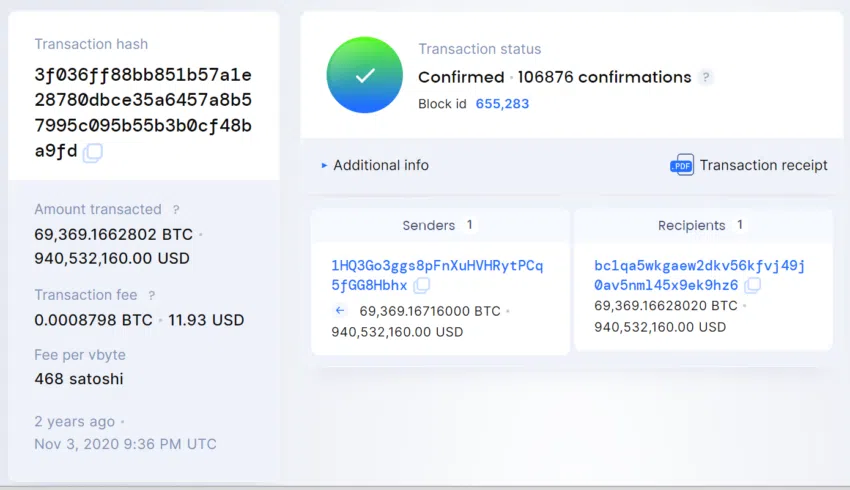
Fast forward to Nov. 2020, crypto forensics firm Elliptic spotted that someone moved 70,000 BTC from a wallet address 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbh. The address is believed to belong to Silk Road because it had received funds from an address belonging to Silk Road in 2013.
The keys to 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbh had reportedly been circulating on hacker forums, embedded in an encrypted file. Since Ulbricht was in prison, he couldn’t have moved the funds. Instead, a hacker likely cracked the encrypted file to access the funds. Analytics firm Chainalysis identified that the hacker had started moving funds out of Silk Road to their own wallets in 2012. None of Silk Road’s logs included their transactions, increasing suspicion that they were the work of a hacker.
The U.S. Treasury Department’s Internal Revenue Service later seized all the funds, worth $1 billion at the time.
In 2021, prosecutors signed an agreement with Ulbricht that the money seized from the hacker would pay Ulbricht’s $183 million in restitution. This debt cancellation means that any funds Ulbricht earns while still in prison he can send to family and friends. Additionally, when he is released, he will not owe any money.
Investigators are upping their game
In the Silk Road investigation, authorities abandoned tried-and-tested methods. Instead of beginning with probable cause against an identified suspect and using a search warrant to get more evidence, they had first to obtain proof from the Silk Road site and track down suspects.
Since then, investigators have adopted state-of-the-art tracing tools for cryptocurrency crimes.
While cryptocurrency transactions are public, investigators often need to look for links between the transactions and other internet activity to identify suspects. To do this, sometimes they go undercover on the dark web using accounts previously seized by authorities to mask their identities. Linking crypto transactions to individuals still requires a fair amount of technical expertise, though.
To help with this skills shortage, the Federal Bureau of Investigation launched the Virtual Asset Exploitation Unit to provide agents with tools and training to track fund flows on the blockchain.
“Even in cyberspace, the Department of Justice is able to use a tried and true investigative technique, following the money,” said Lisa Monaco, second-in-charge at the Justice Department, in Feb. 2022.
Disclaimer
All the information contained on our website is published in good faith and for general information purposes only. Any action the reader takes upon the information found on our website is strictly at their own risk.