Self-sovereign identity is a concept that refers to the use of distributed databases to manage PII.
The notion of self-sovereign identity (SSI) is core to the idea of decentralized identity. Instead of having a set of identities across multiple platforms or a single identity managed by a third party, SII users have digital wallets in which various credentials are stored and accessible through reliable applications.
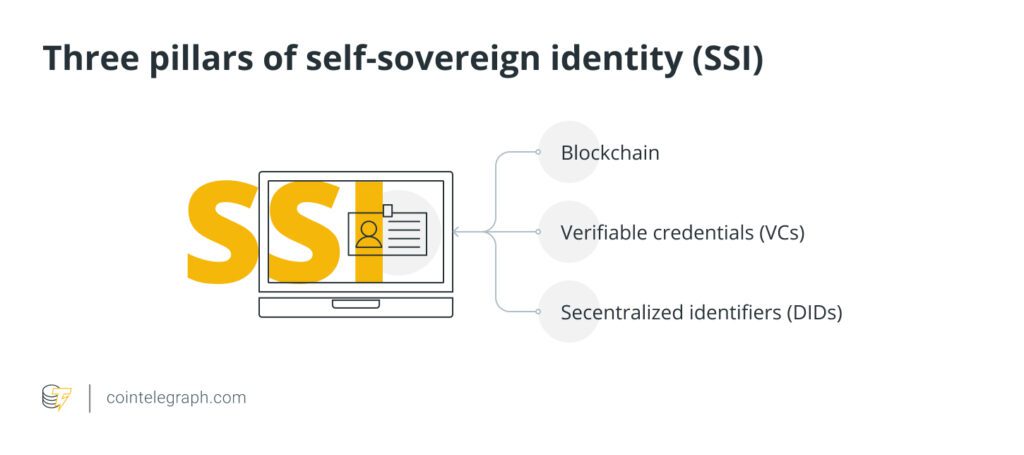
Experts distinguish three main components known as the three pillars of SSI: blockchain, verifiable credentials (VCs) and decentralized identifiers (DIDs).
Blockchain is a decentralized digital database, a ledger of transactions duplicated and distributed among network computers that record information in a way that makes it difficult or impossible to change, hack or cheat.
Second, there are VCs referred to as tamper-proof cryptographically-secured and verified credentials that implement SSI and protect users’ data. They can represent information found in paper credentials, such as a passport or license and digital credentials with no physical equivalent, such as, for instance, ownership of a bank account.
And last but not least, SSI includes DIDs, a new type of identifier that enables users to have a cryptographically verifiable, decentralized digital identity. A DID refers to any subject like a person, organization, data model, abstract entity, et cetera, as determined by the controller of the DID. They are created by the user, owned by the user and independent of any organization. Designed to be decoupled from centralized registries, identity providers and certificate authorities, DIDs enable users to prove control over their digital identity without requiring permission from any third party.
Alongside SII, which is rooted in blockchain, DIDs and VCs, decentralized identity architecture also embraces four more elements. They are a holder who creates a DID and receives the verifiable credential, an issuer that signs a verifiable credential with their private key and issues it to the holder, and a verifier that checks the credentials and can read the issuer’s public DID on the blockchain. Moreover, a decentralized identity architecture encompasses special decentralized identity wallets that fuel the whole system.
How decentralized identity works
The basis for decentralized identity management is the use of decentralized encrypted blockchain-based wallets.
In a decentralized identity framework, users utilize decentralized identity wallets — special apps that allow them to create their decentralized identifiers, store their PII and manage their VCs —instead of keeping identity information on numerous websites controlled by intermediaries.
Besides distributed architecture, these decentralized identity wallets are encrypted. Passwords to access them are replaced by non-phishable cryptographic keys that do not represent a single weakness in the case of a breach. A decentralized wallet generates a pair of cryptographic keys: public and private. The public key distinguishes a concrete wallet, while the private one, which is stored in the wallet, is needed during the authentication process.
While decentralized identity wallets transparently authenticate users, they also protect users’ communications and data. Decentralized apps (DApps) store PII, verified identity details and the information needed to establish trust, prove eligibility or just complete a transaction. These wallets help users give and revoke access to identity information from a single source, making it faster and easier.
On top of that, this information in the wallet is signed by multiple trusted parties to prove its accuracy. For example, digital identities can get approval from issuers such as universities, employers, or government structures. Using a decentralized identity wallet, users can present proof of their identity to any third party.